Data Security for Deployments
Microsoft 365 App Certification
ChimeV5 is a Microsoft 365 Certified App. Out of 1,400+ apps in Microsoft Teams Store only 4% have this This means that your company will have the assurance and confidence that data and privacy are adequately secured and protected when the app is introduced to your Microsoft 365 platform through Microsoft Teams and is fully backed by Microsoft. This Microsoft 365 Certified app has been reviewed by Microsoft against industry standards and controls for security, compliance, and data handling practices. More Information
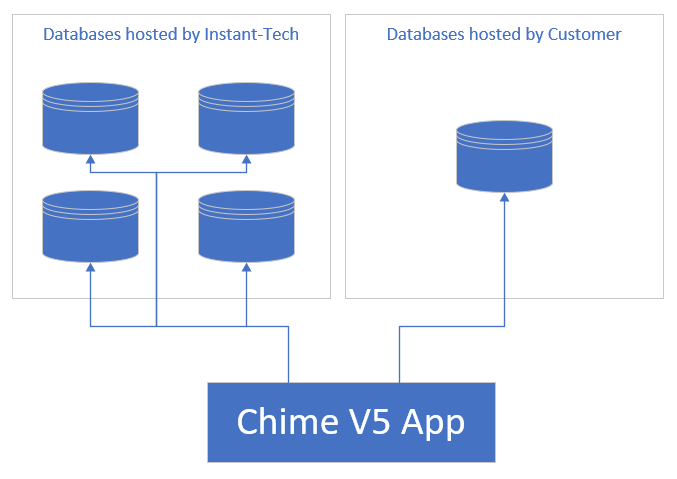
Sectioned out Customer Databases
Using completely separate database instances for each tenant ensures robust data isolation, tailored configurations, and enhanced performance for each customer. This approach allows for greater flexibility in meeting tenant-specific needs while maintaining a high standard of data protection. It also simplifies compliance with industry regulations and builds trust by safeguarding customer information effectively.
Data Security Benefits:
Each tenant’s data is fully isolated, eliminating risks of accidental overlap or unauthorized sharing
Access Control is easier to manage when each customer tenant is it’s own unique environment
Dedicated databases enable tuning and scaling specific to a tenant’s usage and requirements.
Customers have the option to host their own database
Tenants have clear assurance that their data is managed in an environment completely separate from others.
For more information on SAAS solutions to database tenancy, check out this Microsoft article on Multitenant SaaS database tenancy patterns
User Authentication into Tenants is Secured Through Azure Entra/Active Directory
When an instance is created, O365 Admin consents to the use of Graph API permission needed to enable Azure AD/Entra login for the web application. Using Azure Entra/Active Directory for user authentication provides a secure, enterprise-grade identity management solution. It leverages advanced security features such as multi-factor authentication (MFA), conditional access, and threat detection to protect user accounts from unauthorized access.
By centralizing identity management, it ensures consistent access control policies across the organization while simplifying user onboarding and offboarding. Additionally, it integrates seamlessly with other Azure services, offering robust security monitoring and compliance support.
Azure Permissions requested when your tenant is configured - Your Azure Admin will need to go to the login page and will be prompted to consent on behalf of your organization. Enable Azure login for the web app with Graph API permissions
[ email - Delegated ] [ openid - Delegated ] [ profile - Delegated ] [ User.Read - Delegated ]
No User Data is Ever Used to Train AI
We ensure that no user data from our product is ever used to train AI models. By leveraging Azure OpenAI, Azure Blob Storage, and Azure AI Search, we layer your data securely on top of pre-trained AI models, ensuring full data isolation. This approach allows the AI to deliver insights and functionality specific to your data without altering or influencing the underlying model. Your data remains entirely within your control, safeguarded by Azure’s enterprise-grade security and compliance standards. Learn more about the Bring your own data features we are using.
Key Benefits:
Data Isolation: Your data is never integrated into the AI model's training process.
Privacy Protection: Ensures compliance with privacy regulations and keeps sensitive information secure.
Custom AI Functionality: Delivers tailored insights based on your data without compromising its integrity.
Trusted Platform: Built on Azure’s secure infrastructure, leveraging industry-leading encryption and compliance.
Scalable and Secure: Easily integrates with your existing workflows while maintaining strict data security.
Access Control List Customization for Customer-Specific Content
We use Access Control List (ACL) customization to ensure that you can customize which users are able to see content. If it is for internal use, you can set only Azure AD-authenticated users have access to customer-specific FAQ content, PDF documentation, and chat interactions. Alternatively, you can have some content open to
By integrating with Azure Active Directory (Azure AD), we can enforce precise role-based access control, ensuring that sensitive resources are only visible to authorized users. This approach guarantees that each customer’s data and support resources are securely accessed within their organization’s authenticated user base.
Key Benefits:
Secure Access: Ensures only verified Azure AD/Entra users can access sensitive content.
Role-Based Permissions: Enables fine-grained control over which users can view specific FAQs, documents, or chat history.
Seamless Integration: Works natively with Azure AD/Entra for consistent authentication and access management.
Enhanced Privacy: Prevents unauthorized sharing or access to customer-specific materials.
Customizable Control: Easily adaptable to unique organizational requirements or user roles.